This article is from forkast.news and the original article can be read here
A North Korean hacker at the heart of the espionage scandal engulfing South Korea may have covered his/her tracks, thanks to a loophole in the country’s recently-introduced ‘Travel Rule,’ Forkast learns.
An active-duty military officer in the South Korean Army and a digital asset exchange executive leaked confidential information to an agent working for the Democratic People’s Republic of Korea (DPRK) in exchange for Bitcoin, Seoul alleges.
On Thursday, the Seoul prosecutor’s office said that it had charged the South Korean Army captain and the chief executive officer of the unnamed cryptocurrency investment firm for violating the country’s National Security Act.
The alleged incident occurred earlier this year in January.
The first known case of a South Korean military officer assisting North Korea in its attempts to undermine the country using social networking and cryptocurrencies is likely to impact the hard-earned legitimacy Bitcoin and other cryptocurrencies were starting to have with governments and regulatory agencies around the world.
It is further likely to taint the sector even as onerous know-your-customer norms and anti-money laundering and anti-terrorist financing norms stifle innovation and speed of development.
Bitcoin Gate
The 29-year-old Army Captain photographed and leaked military secrets with a burner phone. He turned to the device after the quality of pictures from a wrist watch with a hidden camera was deemed to be too poor. The watch was allegedly procured by the 38-year-old crypto exchange CEO.
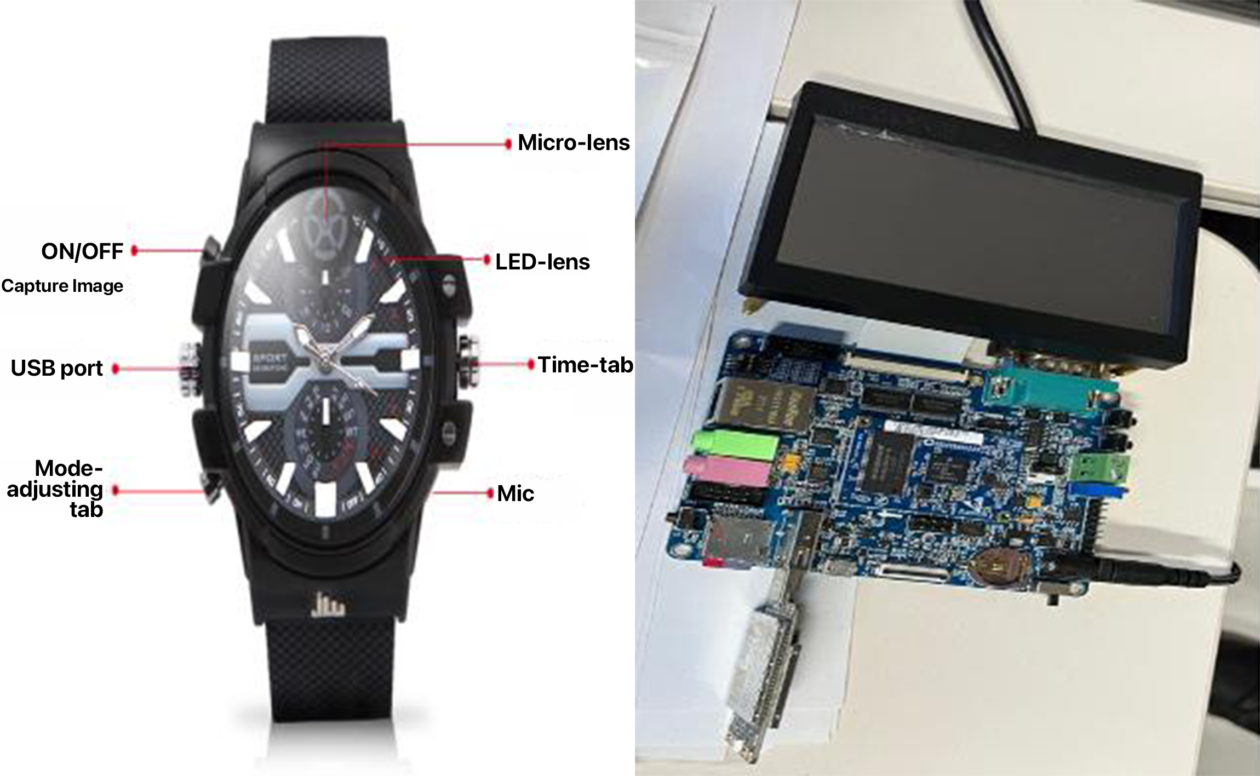
The army officer received about 48 million South Korean won (about US$38,000) in Bitcoin while the crypto executive received about US$600,000 in crypto from the North Korean hacker via a foreign crypto exchange, the prosecutor’s office.
The affair started when the Army Capitan, saddled with debts due to a gambling addiction, met the hacker on a social network in 2020.
Forkast learns that the North Korean hacker instructed the crypto executive to install a hacking device named the ‘Poison Tap.’
The software would have granted the hacker, and North Korea in turn, access to the Korean Joint Command and Control System (KJCCS), South Korea’s super-critical internal military network. The compromised army captain had the security clearance to log into the system, Forkast learns.
The national defense ministry says that if the hack was successful, it would have seriously undermined South Korea’s national security.
See related article: North Korea hacked US$400M of crypto in 2021, says Chainalysis
The two Koreas have never officially ended their 73-year war, maintaining standing armies on the ‘38th parallel,’ the popular name given to 38 degree North latitude in East Asia that demarcates the two countries.
“But the defense ministry was able to seize the attack preemptively,” the ministry official told Forkast.
However the development offers a glimpse into the increasingly sophisticated means at the disposal of the North Korea regime in its attempts to use cryptocurrencies to earn money through illegitimate means as well as undermine the security of its foes and rivals.
American agencies attributed the US$620 million hack on Axie Infinity’s Ronin blockchain to North Korea’s Lazarus Group. An unreleased United Nations document cited by media alleged that the stolen funds are being used to fund the DPRK’s nuclear and ballistic missile programs.
Cloak of anonymity
While the Seoul Central District Prosecutor’s Office has successfully booked the military officer and the crypto executive jointly with the police agency and the Ministry of National Defense, Forkast learns that the North Korean hacker behind this national security-threatening scheme has covered his/her tracks.
“There’s still no progress in tracking the North Korean agent,” a representative of the Ministry of National Defense told Forkast. “It’s because the agent and the two defendants communicated on Telegram, and transacted in Bitcoin.”
“Telegram does not really cooperate with the investigation, it guarantees full anonymity and privacy,” said Hwang Suk-jin, professor of information security at Dongguk University.
“And since the funds were delivered in Bitcoin, [the investigation] needs to track the digital wallets to see where the money originated from, and how it’s been circulated,” Hwang told Forkast. “But South Korea’s Travel Rule mandate does not trace transactions between individual wallets.”
See related article: South Korean crypto businesses scramble to meet FATF travel rule
South Korea recently made the Financial Action Task Force’s (FATF) ‘Travel Rule’ a requirement.
The rule requires South Korean exchanges to collect a sender and receiver’s personal information for all transactions over one million Korean won (US$794.28). But this rule does not apply to peer-to-peer trades.
A police agency official told Forkast that the joint investigation with the prosecutors and the Defense Security Support Command (DSSC) will continue.
Notwithstanding that, experts believe the incident will only make know-your-customer (KYC) norms more onerous for cryptocurrency firms, even as South Korean banks were trying to be more directly involved in the sector.
See related article: South Korean banks seek green light on crypto
Jisu Park, chief executive officer at blockchain security firm Sooho.io told Forkast that there are inevitable loopholes that can enable bad actors in any transactions, whether it be crypto or fiat.
“However, we’re seeing a positive path among regulators to impose more stringent AML/KYC requirements on exchanges, and even on wallets as they institute their own financial products,” Park said.
